Two-Factor Authentication, also known as 2FA, is a complicated name for a relatively simple concept. It’s so simple, in fact, that you’ve probably used it before and not even known it.
In this first article of my two-part series we will learn the basics about 2FA–what it is and why it protects you. The second article (coming in a week or two) will cover how to set up 2FA on important accounts.
Let’s start at the beginning.
What is Two-Factor Authentication?
2FA is the idea that you need two separate pieces of information to log in to one of your online accounts. One of those pieces of information is your username / password combination. Yes, technically, a username and a password is already two pieces of information but since usernames and passwords are hacked frequently and shared freely online, for better security, we consider those only one piece of info and add another level of verification. That second level of verification could be a text message sent to your phone, an automated phone call, an authentication token (e.g. shared set of numbers that change every handful of seconds), a hardware key, or other form of digital ID that only the proper owner would have. Let’s talk about each of these in turn:
- Text Message To Your Phone: This is the form of 2FA that you have probably used before. You enter your username & password into a website (your bank for example) and the website sends you a code–usually six numbers–that you have to type in to complete the login process.
- Automated Phone Call: Nearly the same thing as the text message, an automated phone call simply uses a robotic voice to read out numbers that you’re supposed to type into the website, or to ask you to type a known piece of information (last 4 digits of your social security number, for example) into the phone keypad.
The advantage of using your mobile phone–either voice or text message–for authentication is that most people typically have their phone with them at all times. It’s easy to read a message and type that number into a box on a webpage. The disadvantage is that mobile phone SIM cards can be cloned which means that a very determined and very skilled thief could receive those same authentication text messages and phone calls.

- Authentication Token: This can be an app on your phone or a physical device with a digital screen. (Sometimes known as an RSA SecurID key.) It’s the same process as the text message except that nothing is sent to you. The website server and your phone app (or RSA key) have previously shared information and they have a synchronized set of numbers that they both use. The numbers change every 60 (or so) seconds and you must enter the correct number to complete the login process.
Authentication tokens have the advantage that they cannot be cloned and no two are the same, so a thief absolutely must have your token to log in with your credentials. However, this is just one more “thing” that you have to carry and keep track of. Also, if you lose it, you’re in pretty big trouble because you will not be able to log in to your accounts. A nice bridge between mobile phone text messages and a hardware token is an authenticator app. It’s an app that lives on your phone but acts just like a separate hardware token.

- Hardware Key: A hardware key is a USB device that you must physically plug in to the computer you are currently using to complete the login process. Often they look similar to a USB memory stick. Yubico is one popular brand as is Google’s Titan Key.
A hardware key is the quickest and easiest method of two-factor authentication. All you have to do is plug in the key and you are automatically authenticated into the website. Arguably, this is also the most secure of the 2FA methods since there are no numbers or passcodes for a thief to copy down. Like an authentication token, however, it’s one more thing to keep track of and you’re kind of hosed if you lose it.
Why Should I Use 2FA?
You already know the answer to this question. Security. “But wait,” you say. “Why would anyone want to access my online accounts? I’m not important.” Oh really? You never access your bank account through your web browser? You don’t have a few bits of information or a photo or two that no one should know about stashed away in a social media account somewhere? You wouldn’t be embarrassed (or lose your job) if your boss received a message from your email address with a couple of compromising photos attached?
Seriously, though… Bad guys will be bad guys. They do not need a reason to turn your life upside down, they just will. Your job is to make it harder for them to do so and to save yourself some headaches in the process.
Google, along with researchers from New York University and UC San Diego, conducted a study on the efficacy of two-factor authentication. This is a one-sentence summary of their results:
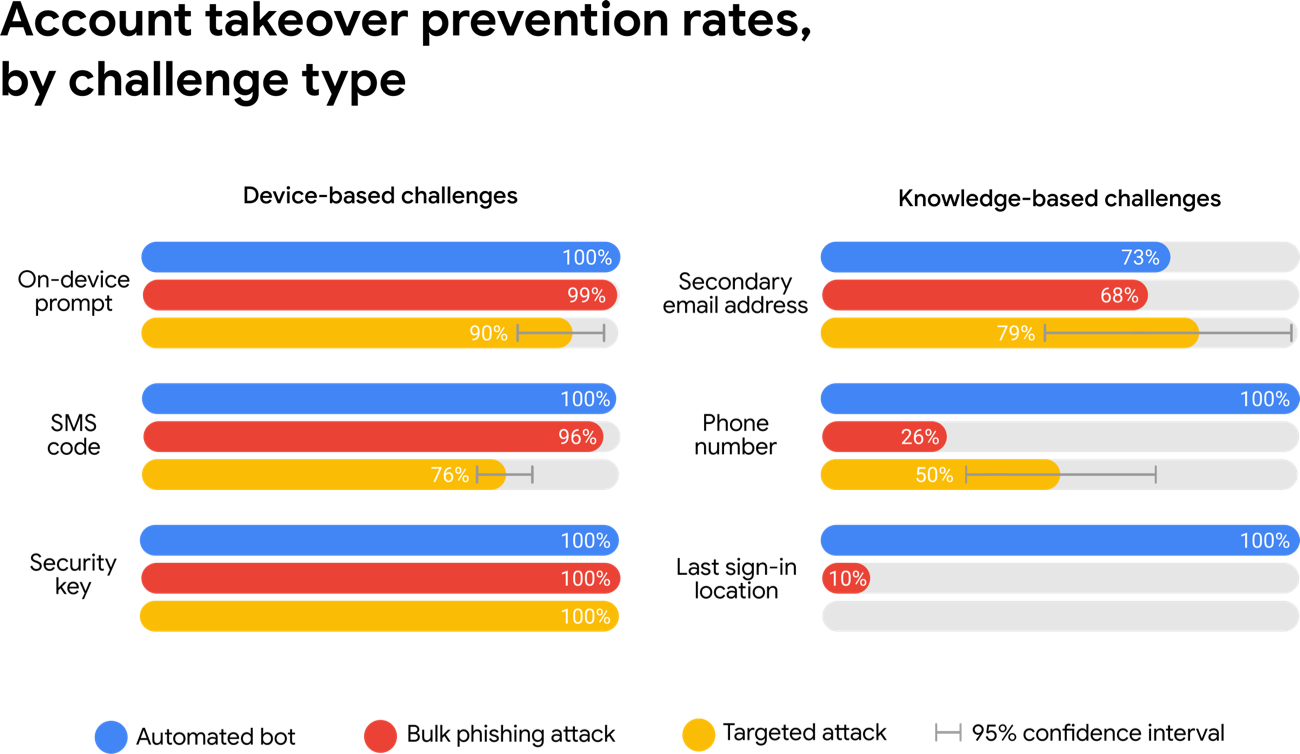
On-device prompts, a more secure replacement for SMS, helped prevent 100% of automated bots, 99% of bulk phishing attacks and 90% of targeted attacks.
https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html
Further, their research shows that using a security key blocks 100% of every type of attack they studied.
I use 2FA on all of the critical sites I use and many that really aren’t so critical. It takes an extra ten or so seconds to type the 6-digit code from my phone into the webpage when I log in. That’s time well-spent in my book.
Come back in a couple of weeks and I’ll show you how to set up 2FA on a website or two. Once you get used to it, you’ll hardly notice the extra step.
UPDATE: 2021-09-23. I’ve written a short update to this article with some additional information and tips. Give it a read here.

Leave a Reply